2018-33: Enhance the SSO Proxy Sign-In Page with a Template with College Co-Branding
| Request No. | 2018-33 |
|---|---|
| Date of Request | June 28, 2018 / August 2, 2018 |
| Requester | Dave Stephens, Butte College |
| Application(s) | SSO Proxy |
| Section / Page | |
| Proposed Change to Download File | N/A |
| Proposed Change to Residency Logic | N/A |
Problem / Issue
Butte College has concerns about the current SSO proxy workflow, especially with respect fo students on their way to Canvas. They called a couple meetings with the Tech Center to report their issues and request a series of changes to help improve the proxy workflow process and ensure SSO is in place across the board. Their goals are both long-term and immediate. Ultimately, requesting UI enhancements to the SSO Proxy sign-in page to better clarify to students where they are and why they are being re-directed there. Their immediate need is to get their students through the proxy to Canvas. They have a marketing campaign underway and a checklist of tasks to prepare students before classes start in the fall.
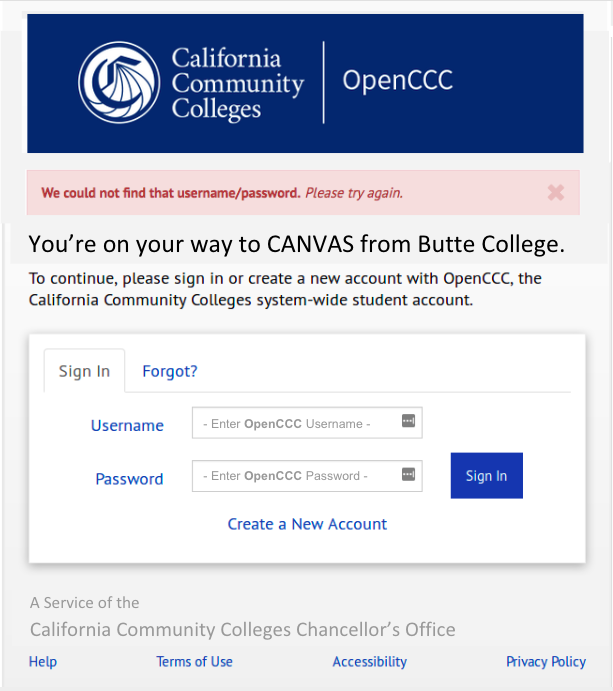
Students are getting confused by the Proxy Sign-In page - the feedback is that it's a disconnect when they get redirected to the proxy. The URL domain changes from a Butte College domain to something unknown (openccc.net). Students complained to their help desk with comments, "Is this legitimate?". They don't see anything familiar on the page: they don't see Butte College (which they have already signed in to), they don't see Canvas logo or URL (which they were supposed to be on their way to); they don't see any messaging or help text that gives them confidence that they are on a credible site and what we are asking is a credible source
Meeting 6/19: First meeting with Butte and ES team
Meeting 6/28: List of issues were discussed and they asked for certain things to be considered, and if possible, completed by August 1, 2018.
Meeting 8/2: Follow up meeting to review progress on change requests. Butte reiterated the following concerns:
- Reiterated that the college co-branding is needed. College logo branded header is the best decision.
- Reiterated the amount of concerns from students saying "Is this legit?"
- Reiterated need for a short embedded video (why am I here?)
- add the college co-branded logo to this page (coming from MIS code)
- Add language that this is a ONE time process, your data is safe
- SSN (comment that they understand the importance of the SSN, but which we could do something about that
- Add a canvas or other app logo next to the banner/header of the page
- Add some clarifying language to the sign in fields to identify OpenCCC sign-in creds
Change Request Specifics
# | Issue/Request | Response / Solution | Responsible | Deadline / Status |
|---|---|---|---|---|
| 1 | Whitelist faculty and staff from being redirected to OpenCCC (from Proxy) when signing in to Canvas | Butte College and others have been whitelisted from the proxy for any session that sends over any EduPersonAffiliation attribute that is not strictly "student" (i.e., that includes - faculty, staff or member or any other value that is not ONLY student). Butte College and others have been whitelisted from triggering the proxy for faculty, staff, member. 8/2 Note: Butte College will do another round of tests - to ensure the whitelisting is in place as expected. Currently, the following logic is in place:
| Franz / Matt | DONE COMPLETE Zendesk #12988 In July, Canvas was whitelisted (does not redirect) for any EduPrimary Affiliation that was not strictly (only) STUDENT. |
| 3 | Improve the language/messaging on the proxy Sign-In page that affirms that the OpenCCC and CCC ID mechanisms are legitimate.
| Proposed Solution: Enhancements to the proxy sign-in page have been approved:
Solution Issues: The Proxy can't differentiate between individual colleges (origin) if they're from a multi-college Tim added to this design - "You're on your way to CANVAS from <<college>>" | IN-PROGRESS | |
| ||||
| See the specifications below the screenshot in the next column: |
For reference, this is the way it looks today (below): Change to:
| |||
Improve the proxy workflow with better branding
Note: When a user goes to access an App like Canvas - then hit the Proxy - Proxy LOGIN - (CCCCO logo has little value to students) - the page presented needs to confirm and legitimize the re-direct. “You’re here because….” Drop icons onto the OpenCCC Login page - (some kind of branding) | Make the following changes to the proxy workflow:
Solution Issues: The Proxy can't differentiate between individual colleges (origin) if they're from a multi-college | IN-PROGRESS | ||
| Fix all proxy bugs and issues in Pilot and Production | Hotfix 1.9.1 - Rolled to Pilot Hotfix 1.9.2 - Pilot release 8.16.18 / Production 8.23.18 5pm TBD | IN-PROGRESS | ||
Fix and deploy EPPN > CCCID API and other processes of getting colleges the CCCIDs created during proxy re-redirect Implement a better way to implement the PROXY | PROXY improvement discussion with Josh on 6/21/18
EPPN issues
Only tells us about mappings that already exist (pulls a list of CCCID to EPPNs) A temp work-around fix was put into place by Infiniti so that State Center can pull down their mappings EPPN/CCCID API problem with capacity (we weren't able to accommodate the counts (too many downloading) EPPN Download Service
(prod-eppn-map) - Suggestions from Matt in proxy meeting 8.02.18 Run something at the college (NOT the download process for applications) Franz to apply confluence page (short term work-around, Jay Owen, increased Dyamo db params to allow State Center to download EPPNs - with approval from Lou. Charles H. fix was more permanent - IF multiple colleges wanted to download EPPN mapping at the same time, even with the increased params there's a chance it could flood the Dynamo again. Increased error handling in the download service code. | |||
Replace the OpenCCC.net domain with .edu or .org (for legitimacy: .com and .net are all easy to obtain and commonly used in spoofing efforts
| Patty discussed obtaining a .edu domain with Tim on 8/1. This is not possible; only accredited institutions can obtain a .edu. Any non-accredited institution that has one now was grandfathered in by EduCause. Sub-domains using the URL-redirect can be implemented if needed | Patty / Franz | DECLINED DECLINED .edu can't be obtained PENDING sub-domain use | |
Gather data on Proxy usage
| I have filed ZD-2850 to request that Infiniti make the Prod Proxy logs available in a S3 bucket so that I can download them and parse for this type of information. I have also asked Infiniti for a dump of the prod eppn_mappings table to see if there is any useful info in there to help answer these questions (IADO-842). | IN-PROGRESS | ||
Create and publish Proxy FAQs | Butte would link to this page for students FAQs and Direct Account Link to create CCCIDs We need a marketing campaign on the Proxy - video tutorials, workflow diagrams, Matt - calls with the college before they go live with Canvas - go over all implementation details carefully, workflow requirements for students (provide link to the Direct Account Creation) - another message (why your student would see it) | NOT STARTED | ||
| Create Video Tutorial for "proxy redirect" to OpenCCC | Video should demonstrate quickly and clearly: If the OpenCCC proxy is triggered when you attempt to access a systemwide application, here's what happens and why. Three options: |
| Proposed CHANGE Breakdown | |
|---|---|
Changes needed to the Sign-In UI To change the Proxy UI - both the Proxy team and the Apply team need to do work, but OpenApply team would need to do the deployment The proxy needs to send a parameter to OpenCCC to tell the page what to display. Requirements: Apply Jira ticket for the work Deployment: Getting into Pilot would be a problem - so we'd have to go right to Prod if we make changes outside of the 6.2.0 release Can't do RF test - they don't do branching/versioning of old code (due to complexity of our code since last prod/pilot releases) Test in TEST environment (Vicky roll back to 6.1.0 branch maybe) | |
Problems with the Current Proxy - Design & Workflow The Proxy can't differentiate between individual colleges (origin) if they're from a multi-college Tim added to this design - "You're on your way to CANVAS from <<college>>" | |
Spam filter processing of multiple email address accounts. talk to Alejandro
Next Actions
Need a date that this or some version of this ^^ can be implemented for proxy flow
Need to work on the language for the sign-in page
Need to come up with two part solution for Butte:
- FAQ for proxy account creation process
- need changes made by X date for their comm campaign
- message with correct URL to the proxy account creation page
Butte will work with Matt Norris (via Dan Neal - who is heading out on paternity leave BTW) to retest the proxy whitelisting. Need to schedule testing of what the proxy is whitelisting
Proposed Solutions for Long-Term Proxy UI/UX Enhancements
Better Short-Form Account Creation process Use the college's attributes to pre-fill an account Alternate - Recovery process - Before we get Batch processing for New Accounts for colleges: Use SuperGlue to bring back data to create an account
| ||
Talk to Tim: Is/can we lift the requirement on colleges to go through proxy for Canvas until we figure out solutions for current issues? Need a better way to message students about the Proxy and why it's important - Marketing campaign Need a better proxy UI UX - legitimacy and user-friendly process Need to show where they came from, where they are going, and why they landed here Suggestions: Bypass the proxy completely Don't trigger the proxy for students w/out CCCID, instead send the college an email or a report on every student/session that did not have CCCID included. Since these are students already, have the college match up the student with OpenCCCApply download information (or report center) and prompt the student to create an account |
Suggestions
The Tech Center needs to be a better job of product marketing, placement, overall management of the proxy.
Colleges need to understand that Faculty & Staff might need to be redirected to OpenCCC if they are truly students in some capacity. For now we can whitelist but ultimately, the proxy is doing what it's supposed to do - which is any "student" needs to have an account (CCCID) and that needs to be passed through to the endpoint (application).
Notes
From 8.02.18 meeting: 9+ colleges provided feedback to Dave Stephens on the use of the proxy - concerns about abandonment when they get to the proxy. Most of the concerns and comments were made by staff and FACULTY, who have a strong voice in this process.
Per Matt S. - you can't really test
Query their EduPerson Affiliation in AD to ensure they are passing the correct affiliation. (typically testing isn't done correctly)
Every use case:
- Student only
Faculty only
Staff only
Member only
Faculty/staff only
Faculty/staff/member only
Run a query and bring back all the different EduPerson Affiliations
Flag any that are multi-valued (staff + student) Matt S. could help by providing a Power-shell script
Effort to get this implemented in the upcoming release, a few files were changed (css file change, jss file,
Making this a dynamic template would require a tiny bit more effort
But would require a proxy change as well - because the proxy needs to determine where they are going to, add param over to call this page.
This would require a Proxy hotfix and an OpenCCC Account hotfix
Both are low risk, low effort (Talk to Josh about the college co-branding effort - either adding a banner to the page or adding a Canvas, etc. logo to the page.)
Redesign the setup of the page? This would be to highlight that most of the students who encounter the page are
If the proxy side is setup to send that information - the Apply dev team could update that page in less than a day.
Franz could
Supporting Documentation
1) Update on status of the following OpenCCC enhancement requests (Donohue)
a. Removal and replacement of the .net domain (as .com and .net are all easy to obtain and commonly used in spoofing efforts).
b. Clearer language and/or imagery that affirms that the OpenCCC and CCC ID mechanisms are actually legitimate. (i.e. "We know you might not be expecting this, but...", etc.). This can easily be accomplished by embedding a short (20-30 second) screencast video. c. Consideration of custom subdomains per CCC point of origination in conjunction with (or w/o) #1 above (i.e. "butte.openccc.edu/idp/profile/SAML2/Redirect/SSO?execution=e4s1")
For Internal Use Only
Related JIRAs |
|---|
OPENAPPLY-5638
-
Getting issue details...
STATUS
|