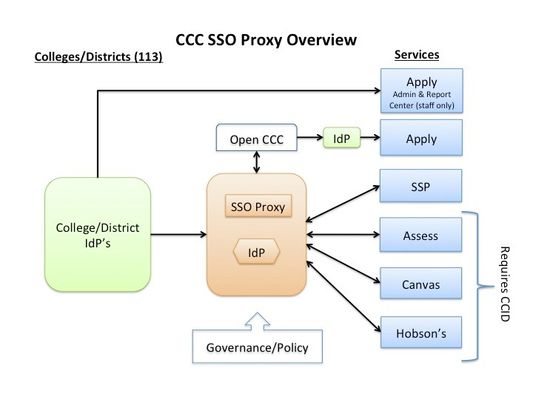
Overview
To support the goals of the CCC SSO Federation, a proxy service has been deployed through which secure CCC web applications can centralize authentication requests for students and staff across all CCC colleges then contact the appropriate "real IdP" - such as the OpenCCC IdP - to complete the requests. The goal of this design is to simplify and accelerate system-wide technology adoption and provide uniform experiences for key users.
The proxy serves two main functions; the first is to include the CCCID as an assertion when the college IdPs are unable to assert the CCCID from their user store. The second is to aid in the discovery process when navigating across service providers in separate domains.Technically speaking, the proxy is designed to help colleges assert consistent SAML attributes to the various Service Providers (SP) within the CCC SSO Federation.
Use Cases
The main proxy use case is when a college is not able to send the CCCID SAML attribute for students. If the Proxy discovers that the student's CCCID is not present when attempting to authenticate to a particular CCC web application, it will attempt to find the CCCID associated with the IdPs unique identifier (EPPN) for the student.
If a CCCID is not found, the student will be redirected to OpenCCC to either recover or create a new OpenCCC account. Once the account is recovered or created, the CCCID will be cross referenced to the student's EPPN so that the next time a student attempts to login to a CCC web application from their college IdP, the proxy will be find the student's CCCID and add it to the SAML attributes presented to other federation service providers.
Functions of the Proxy
The CCC IdP Proxy service is designed to accomplish several things:
Provide a way to add a CCCID attribute to the SAML response to a service, even if the college is not able to provide one;
Provide a central management point where new services can be integrated without each college needing to make any changes to its local IdP in order to access the new service;
Instead of the SAML response from the college/district IdP going directly to the service (e.g. Canvas, Assess), it goes first to the IdP Proxy (which has it own "internal" SP). The IdP Proxy can add attribute(s) to it if needed (e.g. CCCID), filter the attributes received down to the specific attributes needed by the particular service, and send a SAML response back to the service.
This simple diagram illustrates what this looks like:
Before You Begin Integration
Before your college can connect to the CCC SSO, a set of minimum requirements for integration with the IdP Proxy must be met:
- Install an Identity Provider (IdP) software solution such as Shibboleth V3 or Portal Guard, or upgrade your existing Shibboleth IdP to Version 3. (See "Supported IdP Solutions".)
- Schedule a Proxy Integration Kick-Off meeting with the CCC Proxy Project team. See Support for contact information.
- Set up a test environment to use for testing authentication of your IdP with the Proxy and to other CCC web applications.
- Take steps to join the InCommon Federation and register your IdP and upload your metadata.
NOTE: If you have not completed the InCommon membership process by the kick-off meeting, we can still integrate your IdP with the proxy. Once your InCommon membership is complete and your metadata is uploaded to their system, please inform the Proxy Project Team and we will obtain it from InCommon for you.
Install or Upgrade IdP Solution
In order to take advantage of the benefits of Single Sign-On (SSO) and federated identity management, which allows the sharing of information about users from one secure domain to the other organizations and applicatons within the CCC SSO Federation, your college/district must deploy a SAML-compliant IdP which meets the requirements for SSO for students, staff and faculty. For many colleges, this means upgrading your existing Shibboleth V2 IdP (implemented prevously for staff to integrate with the CCCApply Administrator & CCC Report Center) to V3 which facilitates single sign-on for students, as well as staff.
Recommended IdP Solutions
For this purpose, the CCC Tech Center recommends Shibboleth V3. Although any SAML-compliant identity provider (IdP) software solution that meets the requirements of the CCC SSO Federation may be used, support is only provided for Shibboleth and Portal Guard at this time.
For more information about Shibboleth, please see What is Shibboleth IdP? on the CCC SSO Federation Resource Guide and Upgrading Shibboleth from V2 to V3.
Set Up Test Environment
The IdP Proxy and supporting components are currently operational in two environments: PILOT, for testing and early production stage proof of operations; and PROD, the production environment used by students and staff.
In order to complete the integration process and facilitate ongoing testing, colleges must stand up a testing environment to ensure their IdP solution is able to authenticate with the Proxy and CCC applications. The college test environment will access the CCC's PILOT environment for the Proxy and various applications.
Integrating with the Proxy
During the Proxy Project Kick-Off meeting, the following documents will be reviewed to ensure you have a good understanding of the Proxy and how to configure your IdP to integrate with it. Please be sure to discuss all existing and planned implementations with the project team to ensure all systems are connected to the Proxy during the integration process.
- Steps to Integrate with the CCC SSO Proxy
- Attributes for the Proxy: Shibboleth
- Attributes for the Proxy: Portal Guard
- Attributes for the Proxy: Ellucian
- Overview of Attributes for CCC SSO Federated Access
Connecting Web Applications to the Proxy
Connecting to the Proxy From Any Secure CCC Application
When your college is ready to integrate with the Proxy, a series of set up tasks must be completed regardless of which CCC application you are implementing. Please read the documents linked below and schedule your Proxy Project Kick-Off meeting with the CCC Proxy Project Team.
Connecting to the Proxy from Canvas
If your college has imiplemented the Canvas Course Management System, or is planning to implement Canvas, after you complete the initial steps to integrate with the IdP Proxy, you will need to complete an additional set of tasks to integrate Canvas with the Proxy.
The CCC Proxy Project Team will review these steps with you when you meet for your Proxy integration kick-off meeting, Meanwhile, please review the following document and contact the Proxy Project Team if you have any questions.
Before You Begin: Read Integrating with Canvas
Connecting to the Proxy from Hobsons/Starfish
If your college has imiplemented the Hobsons/Starfish Degree Audit System, or is planning to implement any of these education planning tools, after you complete the initial steps to integrate with the IdP Proxy, you will need to complete an additional set of tasks to integrate your Hobsons/Starfish system with the Proxy.
The CCC Proxy Project Team will review these steps with you when you meet for your Proxy integration kick-off meeting, Meanwhile, please review the following document and contact the Proxy Project Team if you have any questions.
Before You Begin: TBD