Clearly, this is a work in-progress.
Overview
The purpose of the California Community Colleges Single Sign-on Federation (CCC SSO) is to provide secure, scalable, and integrated technology solutions for the California Community Colleges that take advantage of economies of scale and facilitated by governance from the colleges themselves. and a common framework for trusted shared management of access to CCC Applications.
Through the CCC SSO Federation, colleges will share in a common framework of shared management of access to secure CCC Application that can give their users single sign-on convenience and privacy protection, while online Service Providers control access to their protected resources.
Federated Identity Management
Federated Identity allows the sharing of information about users from one secure domain to the other organizations in a federation. This allows for cross-domain single sign-on and removes the need for content providers to maintain user names and passwords. Identity providers (IdP) supply user information, while service providers (SP) consume this information and give access to secure content.
At this time, all California Community Colleges already have an Identity Provider (IdP), such as Shibboleth or Portal Guard, in place to authenticate college staff to the CCCApply Administrator and the CCC Report Center. However, to allow students to access the rich portfolio of student services web applications - existing or under-development by the CCC Technology Center - colleges must either install a supported SSO solution that includes student attributes or upgrade their existing IdP to allow students to access the resources within the CCC's SSO Federation.
CCC SSO Federation & CCC Applications
The CCC SSO Federation is a shared federation of CCC colleges .
College applicants, students, staff and faculty will be using the Student Portal, Report Center, Hobsons and Canvas as well as other CCC managed and external services.
Each participating college will be required to provide a SAML compliant Identity Provider to authenticate their user population to these services. Currently, the CCC Technology Center supports Shibboleth IdP software and Portal Guard IdP. For more information, see "Support SSO Solutions".
SSO Participation: Minimum Requirements
Colleges participating in the CCC SSO Federation will be required to implement a SAML-compliant Identity Provider (IdP), become a member of the InCommon Federation; and integrate with the CCC IdP Proxy service, in order to facilitate the full benefits of system-wide single sign-on connectivity for students, staff and faculty across all secure CCC applications.
Optional implementations, but highly recommended, include integration of the College Adapter tool with your student information system to facilitate real-time abc for xyz.
Also recommended is the implementation of MyPath, the Student Services Portal, which serves as the gateway for steamlined user access to all systemwide technology applications for students with single sign-on connectivity.
In addition to the required proc
What is Single Sign On (SSO)?
Single Sign On (SSO) is a session and user authentication process that permits a user to enter one username and password - one time - in order to access multiple applications without having to login to each application separately. For example, when CCC students are configured for SSO, they can login to one application, such as MyPath, the Student Services Portal, and then access multiple different web applications, such as Canvas Course Management System (CMS), CCCAssess, and CCCApply, without having to login separately to each of the applications.
The SSO process involves authentication and authorization. Authentication is a confirmation that the person logging in is the person they claim to be. Authorization is a confirmation that the logged-in person is authorized to access a particular "resource" (i.e. MyPath Portal, etc.). The Tech Center has implemented a CCC IdP Proxy process to facilitate streamline integration for current and future applications.
Why implement SSO?
Implementing an SSO solution is a requirement of the CCC SSO Federation and allows participating California Community Colleges to take full advantage of the products and services offered by the CCC Technology Center (CCCTC) by allowing students, faculty, and staff to access statewide web-based information technology applications via a single sign-on account.
The benefits of SSO include
Integrating with CCC Applications
Because a student will usually initiate access to central services from their home college web site, and to avoid being presented with a IDP discovery page where the student has to choose from 110+ IDPS, the college will provide an IdP initiated SSO link to the the targeted service provider. A central IDP proxy will be invoked in order to save the students last used IDP. When linking out to other Service Providers during the same SSO session, request again will be routed though the IDP proxy so that the target service provider knows which IDP the user came from.
Why implement SSO?
Implementing an SSO solution is a requirement of the CCC SSO Federation and allows participating California Community Colleges to take full advantage of the products and services offered by the CCC Technology Center (CCCTC) by allowing students, faculty, and staff to access statewide web-based information technology applications via a single sign-on account.
The benefits of SSO include
The EduPersonPrincipalName (EPPN) is the unique identifier for a user for across all college IDPs.
For the the Student population, an OpenCCC Account Id (CCCID) is a unique correlation ID for a single student across then entire CCC system and is a key SAML attribute requirement across all service providers. Many colleges will be able to lookup the CCCID from their directory servers, but for the colleges that dont store CCCID, the central IDP proxy will be used to lookup the CCCID for a given EPPN and included it in the list of SAML attributes sent to the final Service Provider.
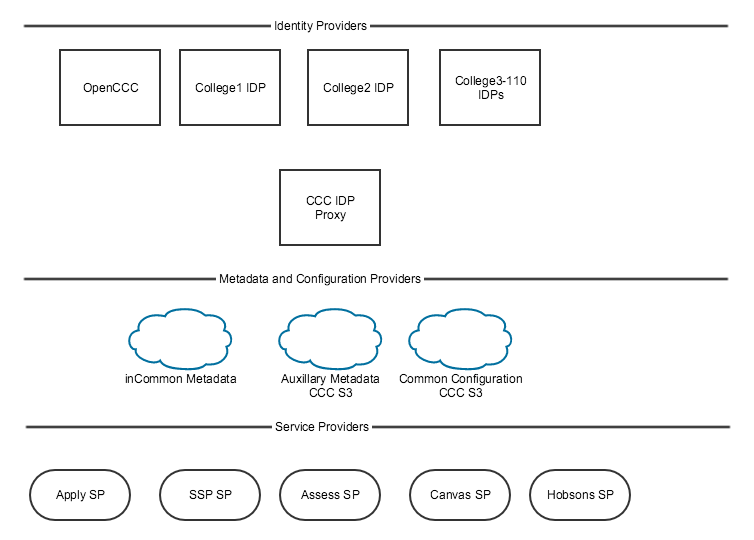
The following diagram illustrated the relationship between Identity Providers (IDP), Services Providers (SP) and Metadata Providers.
What is the CCCID?
A CCCID is a unique student-identifier generated when an individual creates an OpenCCC account, enabling secure, single sign-on access to admissions applications and other systemwide web-based services. The CCCID is commonly created during the admissions application process known as CCCApply, however, any existing student can (and should) be encouraged to create an OpenCCC account and thus create their own CCCID, explained Lou Delzompo, Chief Technology Officer of the CCC Technology Center.
Supported SSO Solutions
To participate in the CCC SSO Federation, colleges must implement an Identity Provider solution that meets the minimum requirements of the Federation. The CCC Tech Center currently supports Shibboleth and Portal Guard identity provider software solutions for student, staff, and faculty SSO. Colleges using an alternate solution should review the CCC SSO Federation IdP System Requirements page to ensure your solution is meeting the requirements necessary to integrate with CCC system-wide applications and the CCC IdP Proxy.
- Shibboleth IdP V3
- Portal Guard IdP
What is Shibboleth IdP?
Shibboleth Identity Provider Software is a single sign-on (SSO) login system that is among the world's most widely deployed federated identity systems and is a supported SSO solution of the CCC SSO Federation. It allows sign in using just one identity (username and password), connecting users to applications both within and between federations of organizations and institutions.
The Shibboleth Internet2 middleware initiative created an architecture and open-source implementation for identity management and federated identity based authentication and authorization (or access control) infrastructure based on Security Assertion Markup Language (SAML).
What is Portal Guard IdP?
Portal Guard Identity Provider Software is a single sign-on (SSO) login system, similiar to Shibboleth, however...
What is the InCommon Federation?
CCC IdP Proxy
The CCC IdP Proxy is a centralized proxy service used to help colleges assert consistent SAML attributes to the various service providers within the CCC Federation.
The main proxy use case is when a college is not able to send the CCCID SAML attribute for students. If the proxy discovers that the CCCID SAML attribute is not present, it will attempt to find the CCCID associated with the IdPs unique identifier (EPPN) for the student.
If a CCCID is not found, the student will be redirected to OpenCCC to either recover or create a new OpenCCC account. Once the account is recovered or created, the CCCID will be cross referenced to the student's EPPN so that the next time a student attempts to enter the CCC SSO Federation from their college IdP, the proxy will be find the student's CCCID and add it to the SAML attributes presented to various federation service providers.
For more information on the central IdP Proxy, please refer to the CCC IdP Proxy implementation guide.
How to Integrate with the CCC IdP Proxy?
What is the EPPN?
The EduPersonPrincipalName (EPPN) is the unique identifier for a user (applicant, student, faculty, staff) across all college IdPs.
For the the Student population, a Central OpenCCC Id (CCCID) is a unique correlation ID for a single student across the entire CCC system and is a key SAML attribute requirement across all service providers. Many colleges will be able to lookup the CCCID from their directory servers, but for the colleges that dont store CCCID, the central IdP proxy will be used to lookup the CCCID for a given EPPN and included it in the list of SAML attributes sent to the final Service Provider.
The EPPN has the syntax of an email address, but it should be considered a "globally unique federated identifier" rather than an email address. It is generally the most important attribute to be shared with federated services. Note that the value of EPPN does not have to match what the user fills in as their username when they login, and the user does not need to know what their EPPN is, as it is shared between the IdP and the service. It should be unique, rarely change, and not be reassigned to another
Supply CCC's with documentation necessary to complete the following:
CCCID configuration
SSO Configuration
College Adaptor Installation
IdP Proxy
Either through in house development efforts or a combination of in house development and contract work, using a mini-grant model of funding.
Supported Configurations
The CCCTC will support the following configurations:
Shibboleth v.3 with InCommon metadata
Portal Guard with InCommon metadata
*Other
CCCID
A CCCID is generated when a student sets up an OpenCCC account and commonly passed to the college in the CCCApply data download.
CCCID is then stored in the college’s SIS or college LDAP/Active Directory
CCCID is passed as an attribute from the college’s IdP to the systemwide applications SP (i.e. Canvas, CCCAssess, MyPath, etc.)
CCCID is used by the systemwide application to identify the student.
SSO Configuration
Correct configuration of Shibboleth / PortalGuard (as appropriate)
IdP Student and IdP Staff
Upgraded to 3.0
Connected to InCommon Metadata
Required - Ability to pass CCCID (Student IdP only)
Ability to pass common InCommon Eduperson Attributes (EPPN Required)
https://www.incommon.org/federation/attributesummary.html
Ability to pass other Eduperson Attributes as available (Optional, but highly encouraged)
http://software.internet2.edu/eduperson/internet2-mace-dir-eduperson-201602.html
-Upgrade of Shibboleth IdP or New Implementation of Shibboleth IdP on client provided hardware and operating system software or Implement items below using client provided installation of PortalGuard
-Configuration of authentication against up to two (2) authentication sources
-Configuration of user attributes, gathering from up to three (3) supported user attribute sources
-Configuration of Metadata using InCommon’s Metadata repository
-Shibboleth Log-In Form branding for new implementations
-Validate current Admin users can authenticate to the Report Center and Administrator using the upgraded IdP
-Enable authentication using the Shibboleth IdP to CCC central services including:
Instructure’s Canvas LMS (CCMS)
OpenCCC Apply Report Center and Administrator via the staff IdP
CCC Student Service Portal (SSP)
CCC Assess
College Adaptor (completed in conjunction with CCCTC)
Pre-Work Questionnaire (completed by college)
Colleague School Questionnaire
PeopleSoft School Questionnaire
Configure Test Environment (completed by CCCTC)
Configure an Adaptor for a New School
College Adaptor Test Script - Windows
Testing (completed in conjunction with CCCTC)
Link to Experis Test Plan
Configure College Adaptor in Production Environment
- Once initial testing is complete and satisfactory; repeat configuration and testing in production environment.
IdP Proxy
- (Need Documentation from UNICON)
- Configure SSO to trigger IdP Proxy when CCCID does not exist
List of Contractors
- Unicon
-
Mini-Grant Funding