Attributes for CCC SSO Federated Access
This page provides a description and examples of the key attributes that are needed to support and enforce appropriate access to CCC SSO federated applications and cloud services. These are the attributes which need to be supported by college/district Identity Providers, and released to various services including the CCC SSO Proxy.
Using Your College Identity to Access CCC Applications and Cloud Services
The Importance of the EPPN: eduPersonPrincipalName
When your users login to services at your college/within your district, they enter a Username and a password. Most commonly that Username is matched against the sAMAccountName or the uid attribute for the user in your Active Directory or other LDAP directory. Sometimes, particularly for students, you might actually have the student enter some other student identifier as their Username. Generally, most colleges don't require their users to add a '@college.edu' type suffix when they enter their Username.
However, for CCC applications, which provide services to many different institutions, having a user identifier that is "globally unique" is very advantageous.
The identifier that has been defined is called eduPersonPrincipalName, or EPPN. It is defined first as part of the eduPerson schema, linked to above. EPPN has the syntax of an email address, and might even "work" as an email address, but its purpose is to be a globally unique federated identifier, rather than an email address. It is generally the most important attribute to be shared with federated services.
EPPN Construction
The standard practice in the Higher Education community is that EPPN is constructed by taking some local campus identifier (often SAMAccountName or uid, but sometimes some other local identifier like an employee or student id number), and adding to it a suffix of the form: @college.edu. That suffix is referred to as the "scope". So the EPPN for Jane Smith, who has a sAMAccountName of jsmith, at Best Community College, which has a campus domain of bestcc.edu, will typically be jsmith@bestcc.edu. But depending on how the college manages the sAMAccountName attribute for its users, if Jane Smith has a student id of 12345678, the college might choose to make her EPPN be 12345678@bestcc.edu instead.
Here are the key considerations to keep in mind in considering what your college/district should use as the EPPN for each of your users:
- The first thing to understand is that what your users enter as their Username to login can still be anything you want it to be, continue to the same as you currently use. There is no need for the user's Username for login to be the same as their EPPN, they are completely independent.
- Standard practice across Higher Education, InCommon, etc. is that every user from the institution has the same suffix for their EPPN, everyone has the suffix @college.edu. It doesn't matter that your staff members have a different email domain than your students. That distinction might be important for email or local needs, but is not an important distinction for "cloud services". The general expectation across federated services is that every user from an institution will have the same scope (suffix) for their EPPN.
- Standard practice across Higher Education, InCommon, etc. is that EPPN is not an actual attribute that you store in your local directory. Instead, within your SAML Identity Provider (e.g. Shibboleth IdP, PortalGuard), you construct the EPPN by taking a campus identifier and adding the scope to it.
- Every user from your institution needs to have a unique EPPN. Now if you manage your staff and students in two different directories, and there is a chance that the same sAMAccountName/uid can occur in both directories, then constructing EPPN by taking the sAMAccountName/uid and adding @college.edu would not necessarily result in a unique identifier for all your users. But remember, you don't have to use the sAMAccountName/uid to construct the EPPN, you could instead use the employee id or student id. Or you could use sAMAccountName/uid for staff, and student id for students, to construct the EPPN – you don't have to use the same attribute to the "left of the @" for all your users.
- The most important properties to consider for choosing the campus identifier(s) to be used for your EPPN are the following:
- unique within your user base,
- never re-assigned to another person,
- persistent, and never (or rarely) changes.
- unique within your user base,
- Examples could be values like jsmith@college.edu or 12345678@college.edu
The Key Link Between EPPN and Provisioning Feeds
Most cloud service providers require the college to regularly send flat files (or sometimes have sync or realtime connections) to the Cloud Service Provider that identify all the users from that college that should have access to that service. The Cloud Service Provider defines a set of fields that you need to fill in for each user. One of those fields will be defined to be the "user id" for that service. That "user id" becomes the key field, the "username", for that user in the Cloud Service Provider user datastore.
The absolute best practice for CCC colleges to follow is to always put the user's EPPN into that "user id" field. Because the Cloud Service uses the identifier that comes from the college/district IdP to match up to that "user id" from the provisioning feed. I.e. the Cloud Service Provider is going to take the identifier you send in the SAML response, and try to find that person in their user datastore. And the identifier you send in that SAML response to the Cloud Service Provider should be that EPPN value. It will greatly simplify the support and smooth functioning of federated identity across the CCC System if all colleges and districts follow the same set of standard practices with regards to integrating with Could Services and CCC-wide Services.
And remember, just because you are sending EPPN as the "user id" to a Cloud Service, and even if the Cloud Service Provider itself refers to that as the "login name", that does not mean that your users are going to have to fill in their EPPN as their Username when they login. EPPN is what we send for them, it is independent of what the user uses to login.
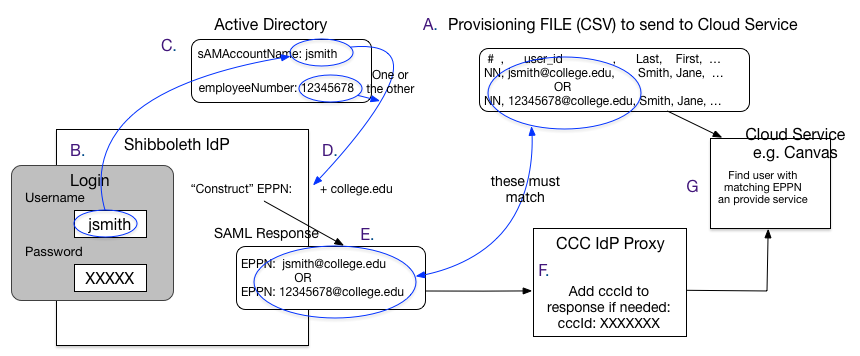
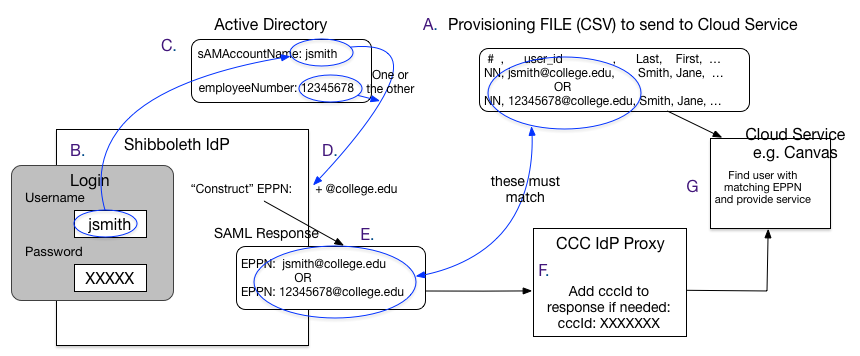
Here is a diagram that illustrates how this all "fits together"
A. College sends provisioning feed to Cloud Service Provider, making sure the "user_id" is going to match what the Shibboleth IdP will send, either the jsmith@collge.edu or 12345678@college.edu.
B. User logs in at college, to the IdP, with their Username (jsmith).
C. User record in AD/LDAP is found, password verified.
D. IdP pulls the needed attributes out of AD/LDAP for the user, including whichever identifier will be used to "construct" the EPPN. It "constructs" the EPPN by taking that identifier and adding the scope for the college to it, in this case "@college.edu".
E. IdP builds and sends the SAML response, including the EPPN.
F. CCC SSO Proxy adds the CCCID to that response if needed, and sends it on to the cloud service.
G. Cloud Service finds the user in its user database (built from the provisioning feed) by looking for the user with the EPPN it just received in the SAML response, and presents that user their information/services.
Attribute Summary
Minimum Required Attributes
Simple Name and the SAMLv2 name when sent in the SAMLv2 response | Short description | Sample value(s) | Description |
|---|---|---|---|
eduPersonPrincipalName (EPPN) urn:oid:1.3.6.1.4.1.5923.1.1.1.6 | Primary federated identifier of a given user from a college/district IdP. | EPPN has the syntax of an email address, but it really is a "globally unique federated identifier", not an email address. It is generally the most important attribute to be shared with federated services. See the above for a much longer description of this critical attribute. | |
eduPersonAffiliation urn:oid:1.3.6.1.4.1.5923.1.1.1.1 | Role within the institution |
| All of the roles a given person has within the college, but only the values defined in the eduPerson schema are allowed for this attribute, you can't make up "new values" for it. The affiliate value identifies a person that has applied to one or more colleges but is not a student yet. This is the only attribute listed here that is intended to have multiple values. All the rest are expected to have a single value. |
uid urn:oid:0.9.2342.19200300.100.1.1 | Username | jsmith | This is usually the value that the user fills in as their username when they login. If you are using AD, the usual attribute you want to use to populate uid is the sAMAccountName attribute. |
givenName urn:oid:2.5.4.42 | First Name | Jane | |
sn (surname) urn:oid:2.5.4.4 | Last Name | Smith | |
displayName urn:oid:2.16.840.1.113730.3.1.241 | Full name to display | Jane Smith | |
mail (email) urn:oid:0.9.2342.19200300.100.1.3 | Email Address | jane.smith@college.edu | |
cccId | The CCCID | The CCCID is a critical attribute for students. If not specified, but required for a portal or service action, the CCCID will be looked up via the EPPN. If no match is found, the action cannot be performed until the user creates a CCCID via the OpenCCC portlet. |
Other Attributes
These are optional attributes that can be sent by the college. There may be a few services that would use these attributes if available. One example use is that these can be used to pre-populate values when the user is required to create a central CCCID account.
Simple Name and the SAMLv2 name when sent in the SAMLv2 response | Short description | Example | values |
|---|---|---|---|
eduPersonPrimaryAffiliation urn:oid:1.3.6.1.4.1.5923.1.1.1.5 | Primary role at the institution |
| 1 |
street urn:oid:2.5.4.9 | Street address | 303 Mulberry St. | many |
| locality .... urn:oid:2.5.4.7 | City | Metropolis | 1 |
| st .... urn:oid:2.5.4.8 | State or Province name | CA | 1 |
| postalCode .... urn:oid:2.5.4.17 | Postal or zip code | 12345 | 1 |
| homePhone .... urn:oid:0.9.2342.19200300.100.1.20 | Home Phone Number | +1 212 555 1234 | 1 |
| mobile .... urn:oid:0.9.2342.19200300.100.1.41 | Mobile Phone Number | +1 775 555 6789 | 1 |