Governance refers to Data Governance in MDM.
What is Governance?
...
| Governance... | |
|---|---|
| references | where the Master Data is stored |
| provides | visibility to data between zones and adaptors |
| contains |
|
...
Operation ACLs are not part of zone data governance. Operational ACLs set policies that set forth for a given data domain version:
- What zone can or can't POST or DELETE data records (DRs).
- What adaptors or can't POST or DELETE data records (DRs).
There is a single system-wide chain for Operational ACLs that is controlled by the DGS. By default all zones and adaptors can POST and DELETE data records but POST and DELETE polices for data records can be controlled by the DGS.
Operational ACL policies can be on the following:
...
A very simple example it illustrate this point:
- There are four three zones: ZoneW, ZoneX, ZoneY and ZoneZ each with only one adaptorZone-X, Zone-Y and Zone-Z each with two adaptors. All adaptors are capable of storing/retrieving data entries for the Customer domain
- ZoneW Zone-X has the following Outbound ACL Chain
| Source Zone | Destination Zone | Destination Adaptor | Domain Version | Policy | ||
|---|---|---|---|---|---|---|
| 1 | ZoneW | ZoneYZone-X | Zone-Y | ALL | ALL | ALLOW ALL |
| 2 | ZoneWZone-X | ALL | ALL | ALL | RESTRICT ALL |
ALL = GET, PUT, POST, DELETE
- A Customer PUT data event is raised on adaptor1 in ZoneWZone-X
- YOUnite can see that the adaptors in ZoneX, ZoneY and ZoneZ are all capable of consuming this data event
- YOUnite attempts to route the data event to ZoneXZone-Y
- YOUnite inspects ZoneWZone-X's outbound ACL chain and gets a match on the first ACL in the chain and routes the event to the adaptor in ZoneXtwo adaptors in Zone-Y
- YOUnite attempts to route the data event to ZoneYZone-Z
- The first ACL does not match but the second does restricting the event, so the data event is NOT routed to ZoneY
- Zone-Z
- YOUnite attempts to route the data event to ZoneXZone-Y
Following is more involved example using the zones and adaptors from above. ACLs are evaluated from first to last, the first match is applied to an incoming data event:
| Source Zone | Source Adaptor | Destination Zone | Destination Adaptor | Domain Version | Data Records | Policy | Notes | |
|---|---|---|---|---|---|---|---|---|
| 1 | ZoneWZone-X | ALL | ZoneXZone-Y | ALL | ALL | ALL | RESTRICT ALL | Restricts all outbound data events to ZoneXZone-Y |
| 2 | ZoneWZone-X | ALL | ZoneXZone-Y | Adaptor1 | ALL | ALL | RESTRICT ALL | This ACL is useless since ACL #1 already restrict all events to ZoneXZone-Y |
| 3ZoneW | Zone-X | ALLZoneY | Zone-Z | ALL | Customer v1 | DR-123, DR-456 | RESTRICT ALL | Restricts the data records (DR-123 and DR-456) from going to ZoneYZone-Z. |
| 4ZoneW | Zone-X | Adaptor2 | ALL | ALL | ALL | ALL | RESTRICT ALL | Restricts data events from flowing out of ZoneWZone-X's adaptor2 to all zones. |
| 5ZoneW | Zone-X | ALL | ALL | ALL | Customer v1 | Customer.ssn | RESTRICT ALL | Restricts a customer's SSN from flowing out of of ZoneWZone-X. |
| 6ZoneW | Zone-X | ALL | ALL | ALL | ALL | ALL | ALLOW ALL | Allow everything else out i.e. if a data event can be delivered to many adaptors in the YOUnite ecosystem it will be delivered to all adaptors except for the restrictions placed by the above ACLs. ALLOW ALL is the default so in reality, this ACL is unnecessary. |
...
After applying all of the above, the end result is:
- ZoneX Zone-Y gets nothing
- ZoneY Zone-Z is restricted from seeing the two DRs listed above
- No data from ZoneWZone-X's Adaptor2 flows to any zones or adaptors
- ZoneW Zone-X never shares Customerthe Customer version 1 Domain property Customer.ssn (for all adaptors in the outbound zones)
...
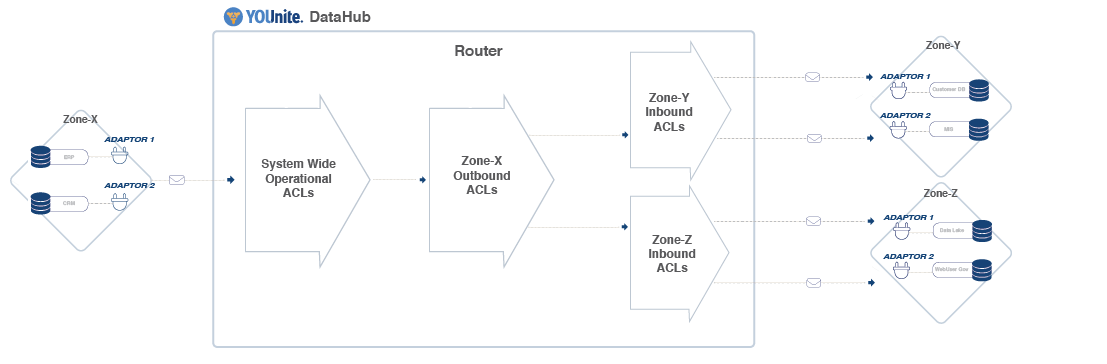
The image below represents the components involved as a data event is detected at an adaptor and flows through the YOUnite ecosystem.
TODO: Simplify this
- On the diagram's left side is a source zone’s single Source Adaptor (abcd-1234) that sends data events (data records) in its domain(s) to the router.Note: A zone can have many adaptorsZone-X, Adaptor 1) detects a data event in the source system (ERP) and sends a data event (data record for a given domain version) to the router.
- The data records record sent from the source adaptor to the router have Operational ACL applied to them. Operational ACL limits which data operations are allowed (create/delete YOUnite Data Records) from the source zone’s adaptor(s) and adaptor domain(s) and are defined by the zone's DGS.
- Next, the data records from the source zone’s domains/adaptors are linked to YOUnite Data Records to avoid data record duplication.
- Note: The data records published by the source adaptor could be updates, deletes, or new records.
- Outbound ACLs then get applied to the source adaptor’s data recordsrecord (Zone-X, Adaptor 1). The Outbound ACLs are defined by the source zone’s ZDS and define what data the Zone can send out (i.e .restricting data, or elements of data, of certain domains from flowing out of certain adaptors in the zone to other zones).
- After Outbound ACLs are applied the data records are published to the YOUnite Data Hub Router and subscribing/desitnation zones and their adaptors (on the diagram's right side) are notified of the updated data.
- Destination zones have Inbound ACLs in place to define which data operations are allowed from source zones and their adaptor(s). Inbound ACL is defined by the destination zone’s ZDS. Any data or operations that are configured to be restricted are filtered out.
- After Outbound ACLs are applied the data records are published to the YOUnite Data Hub Router and subscribing/desitnation zones and their adaptors (on the diagram's right side) are notified of the updated data.