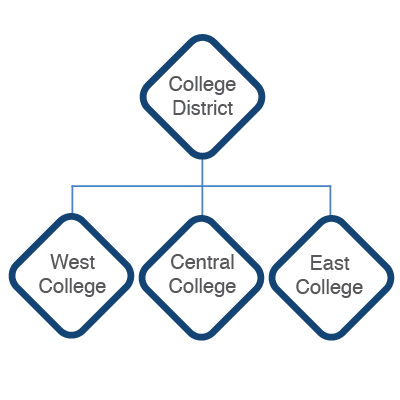
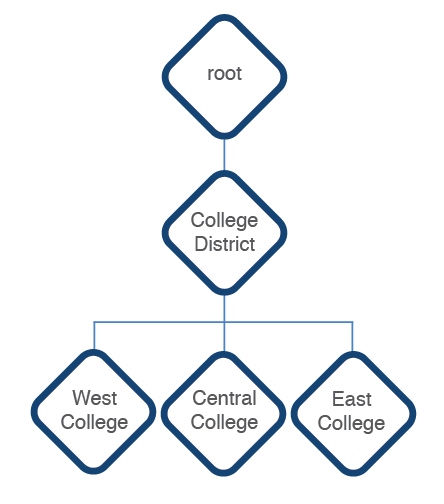
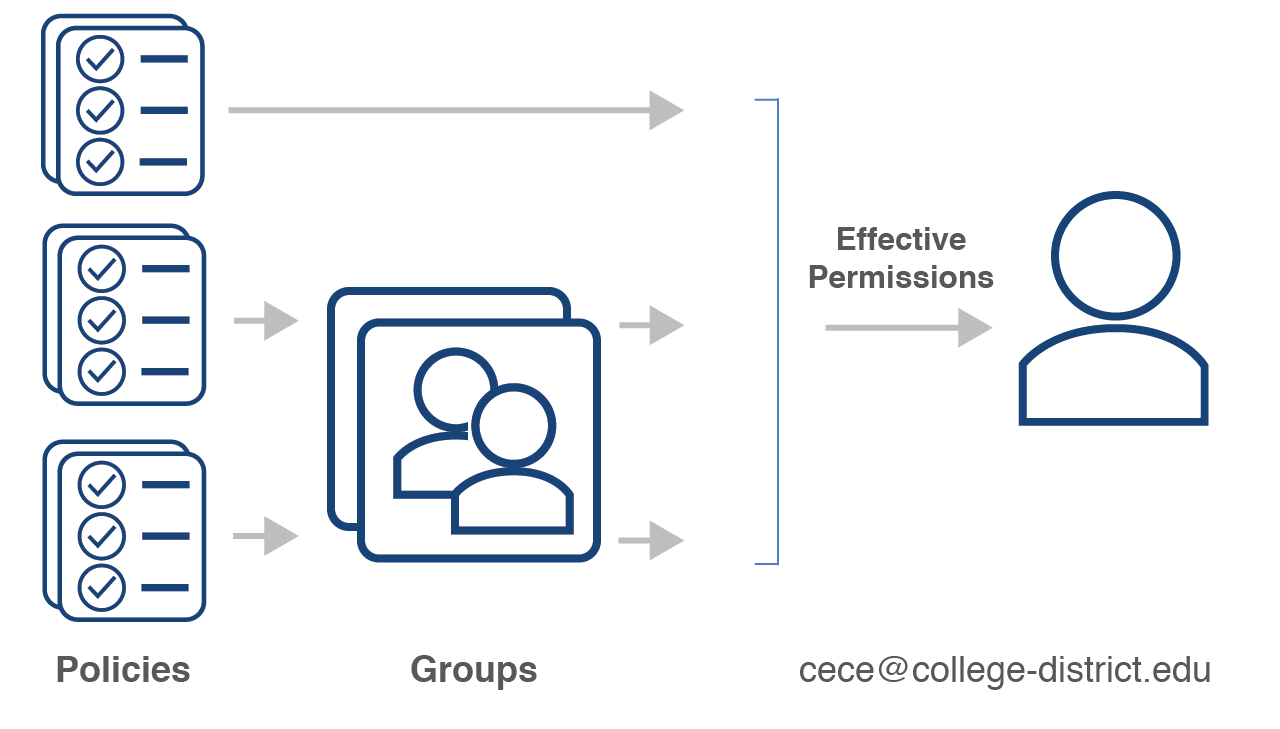
YOUnite can group an organization's resources to mirror the organization's structure (e.g. divisions, departments, districts, etc) and uses these groupings to create relationships within the organization. With YOUnite these groupings are called zones.
It's important to understand the distinction permissions and ACLs:
- Permissions grant access to resources in the YOUnite ecosystem
- ACLs manage access to inbound and outbound data (which is covered in the Governance page).