SAML EntityIDs and Assertion Consumer Endpoints (ACS) for the Proxy
There are two instances of the CCC SSO Proxy that you must configure attribute release to, a Pilot and a Production instance. The entityID for each is:
Proxy Pilot:
Proxy Production:
see Attributes for CCC SSO Federated Access for discriptions of required attribues.
ADFS 3.0+ Custom Claim Creation (custom attribute fields) & Metadata Updates
Note: The CCCProxy uses SimpleSAMLPHP, the first section below is for your reference when connecting to a Shibboleth SP. SimpleSAMLPHP has the same attribute requirements as Shibboleth and the Technet article covers mostly this topic. You can send us your Metadata and we will convert it to the necessary format. You can safely skip the section covering metadata conversion for the CCCProxy integration.
Microsoft has posted this guide for ADFS 2.0, InCommon & Shibboleth integrations. I've modified some of what is listed here to match the requirements for the CCC Proxy. This documentation covers custom claim creation and modifications to AD FS metadata to be compatible with Shibboleth SP. This guide tested with AD FS 3.0 & an early release version of AD FS 4.0. Please read the below linked documentation if you have questions outside what is covered. Use the information provided at your own risk and make sure the steps meet with your security requirements.
https://technet.microsoft.com/en-us/library/gg317734(v=ws.10).aspx
...
| title | AD FS & Shibboleth Metadata |
|---|
In order to for AD FS to be operable with a Shibboleth SP(Service Provider) there are some changes that are required.
...
SAML EntityIDs and Assertion Consumer Endpoints (ACS) for the Proxy
There are two instances of the CCC SSO Proxy that you must configure attribute release to, a Pilot and a Production instance. The entityID for each is:
Proxy Pilot:
Proxy Production:
We will need a copy of your metadata. You can email the URL or a copy of the XML file.
AD FS metdata URL:
see Attributes for CCC SSO Federated Access for discriptions of required attribues.
ADFS 3.0+ Custom Claim Creation (custom attribute fields) & Metadata Updates
Note: The CCCProxy uses SimpleSAMLPHP, the first section below is for your reference when connecting to a Shibboleth SP. SimpleSAMLPHP has the same attribute requirements as Shibboleth and the Technet article covers mostly this topic. You can send us your Metadata and we will convert it to the necessary format. You can safely skip the section covering metadata conversion for the CCCProxy integration.
Microsoft has posted this guide for ADFS 2.0, InCommon & Shibboleth integrations. I've modified some of what is listed here to match the requirements for the CCC Proxy. This documentation covers custom claim creation and modifications to AD FS metadata to be compatible with Shibboleth SP. This guide tested with AD FS 3.0 & an early release version of AD FS 4.0. Please read the below linked documentation if you have questions outside what is covered. Use the information provided at your own risk and make sure the steps meet with your security requirements.
https://technet.microsoft.com/en-us/library/gg317734(v=ws.10).aspx
| Expand |
|---|
| title | AD FS & Shibboleth Metadata |
|---|
|
In order to for AD FS to be operable with a Shibboleth SP(Service Provider) there are some changes that are required. AD FS and SimpleSAMLPHP/Shibboleth have metadata incompatibilities. SimpleSAMLphp/Shibboleth expect inbound SAML attributes names to use a different name format (urn:oasis:names:tc:SAML:2.0:attrname-format:uri) than AD FS publishes by default (urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified) Custom claims need to be mapped which is time consuming.
AD FS Metadata can be modified using https://github.com/rohe/pysfemma The below is an example of the output. You can use the below for testing by modifying. (In production change to meet your needs) but it might be easiest to use adfs2fed.py in the tools directory in pysfemma. In the first line add the ID="Your ID" and entityID="Match your ADFS server" Modify both X509Certificate entries with your certificate information. Replace all references to YourAdfsServer.test.edu with your information.
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" ID="_65f54c67-86fe-453b-830f-273b53cc3aca" entityID="http://YourAdfsServer.test.edu/adfs/services/trust">
<Extensions>
<shibmd:Scope regexp="false">test.edu</shibmd:Scope>
</Extensions>
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="encryption">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>eV1oA6cWOlRGSlCAr2XixPLVpqRA4FS8IViGxSLdGKxsQLQdiFzIZyxf6heZ7pJ2JN/aZdxlOD0YzQPG0cvz/c5mEE2kZc0GWn9/ofLS3ZmYlu/nnoBgygaJgjd/mRd4cS0PVnhFiBtyi13dRE9DqcGMtaSxuSHuUungfu0mF0zcciRvaNr96yrNO585CZiljGGFfp1prlJVAGhQdMGHqtuHibrqxhqPKzIxyRD5rlB5GXTes0hnqz9dnPfY6cRAgMBAAEwDQYJKoZIhvcNAQELBQADggEBANsXE1lTVIDcdnIPRJVxSmKadHzMbDThlKWYJh3m84qUfiDfjt20YHwojtT41Irysr8IKko5goYx7kpBXAWG1zk02FSmoYgrKFl4atbEJVOv+qVs6s32ZrEjvz7CKNCK2slzi1wgyMfvJgDxcVDbgLNnwh5IBpSnrqkHJy86IlqkwsDUCH7lYQvj3dLtF7oFi2KpbW3O2DpwuJANgIoeATq0wRx88DUVBpdS6Sg6ZfTHVOXOkTkFQgN4JmZJhIkM7e/lkdz9ZoVvFjqCbELHiOPaB04UQRNA6JKFKUKCxhlCl6ouAAp4iPzn4Nr1KVK3me7/pK3ZdyQDgDLcPNzuw0E=</X509Certificate>
</X509Data>
</KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>EBAQUAA4IBDwAwggEKAoIBAQCvWpfMCOsjYgkuOwOzCGLjH9bbECRZ6U1uSrtr/xxi54vLaIVhKotqKUN2nKEem8LDMIgi4zlSsqoNgaoKyn7+o99wN+9bD4jd9KZsqSfY4u7DF49MNZ5lydj/yx8jpuXBcvMHstoPQWFRw6HWgm5/vQlmoZrbBjahfPvCajxxJWjYZvjdhEDBaPZcpTeSPsMME8fdEgG07NaUW0EjkI4on9CsNv1RfQkplpDnePa5Swfjv1V5BIOtBZWuCCDIANv+CkRHcpZBvmYVzG/SNOnLMRBp6Skz37+JqlYdzQ0W5NyFoYzzKOqhDndEGxHRUWbujknHqIaD9CkCg2jT16q9AgMBAAEwDQYJKoZIhvcNAQELBQADggEBAIt1d96VNKbxNwjoxjQ678aamseXPoJsusSJpyiwXiVX7OFiESNQrdQ77Xe8wMccKYMZvb7ESUKhOfRBx9sS/nb6WpujCTfeiP+DR9n3QGTDrsPM6+gOK45svKus8zhVb+Ml+I6WC7iGA9WlJj2LMRR989AlcABFv10Bssqan835EU43lQrSnoS9GJTByykO7JuSjNXvgupcREE9BWgJRSfQ9U9P/r9hBVwjWT4K6gtx4Vws48vfEpY19owx09WJFaJIi4SbcTX/Mi1lyk5wmUfR6t+KHj8eoKvoyuqb/eAPjvVlr7Ktw0xOuWxt7IptGwHVV13x8arNkHb/qMrXtb0=</X509Certificate>
</X509Data>
</KeyInfo>
</KeyDescriptor>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0: |
|---|
AD FS Metadata can be modified using https://github.com/rohe/pysfemma The below is an example of the output. You can use the below for testing by modifying. (In production change to meet your needs) but it might be easiest to use adfs2fed.py in the tools directory in pysfemma. - In the first line add the ID="Your ID" and entityID="Match your ADFS server"
- Modify both X509Certificate entries with your certificate information.
- Replace all references to YourAdfsServer.test.edu with your information.
<EntityDescriptor xmlnsbindings:HTTP-Redirect" Location="https://YourAdfsServer.test.edu/adfs/ls/"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://YourAdfsServer.test.edu/adfs/ls/"/>
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:shibmdtc:SAML:2.0:bindings:HTTP-Redirect" Location="https://YourAdfsServer.test.edu/adfs/ls/"/>
<SingleSignOnService Binding="urn:mace:shibboleth:metadata:1.0:profiles:AuthnRequest" IDLocation="_65f54c67-86fe-453b-830f-273b53cc3aca" entityID="httphttps://YourAdfsServer.test.edu/adfs/servicesls/trust"/>
<Extensions> <shibmd:Scope regexp="false">test.edu</shibmd:Scope>
</Extensions>
<IDPSSODescriptor protocolSupportEnumeration<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://YourAdfsServer.test.edu/adfs/ls/"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:protocolassertion">
<KeyDescriptor use="encryption">
<KeyInfo xmlns=" Name="http://wwwschemas.w3xmlsoap.org/2000ws/09/xmldsig#">
<X509Data>
<X509Certificate>eV1oA6cWOlRGSlCAr2XixPLVpqRA4FS8IViGxSLdGKxsQLQdiFzIZyxf6heZ7pJ2JN/aZdxlOD0YzQPG0cvz/c5mEE2kZc0GWn9/ofLS3ZmYlu/nnoBgygaJgjd/mRd4cS0PVnhFiBtyi13dRE9DqcGMtaSxuSHuUungfu0mF0zcciRvaNr96yrNO585CZiljGGFfp1prlJVAGhQdMGHqtuHibrqxhqPKzIxyRD5rlB5GXTes0hnqz9dnPfY6cRAgMBAAEwDQYJKoZIhvcNAQELBQADggEBANsXE1lTVIDcdnIPRJVxSmKadHzMbDThlKWYJh3m84qUfiDfjt20YHwojtT41Irysr8IKko5goYx7kpBXAWG1zk02FSmoYgrKFl4atbEJVOv+qVs6s32ZrEjvz7CKNCK2slzi1wgyMfvJgDxcVDbgLNnwh5IBpSnrqkHJy86IlqkwsDUCH7lYQvj3dLtF7oFi2KpbW3O2DpwuJANgIoeATq0wRx88DUVBpdS6Sg6ZfTHVOXOkTkFQgN4JmZJhIkM7e/lkdz9ZoVvFjqCbELHiOPaB04UQRNA6JKFKUKCxhlCl6ouAAp4iPzn4Nr1KVK3me7/pK3ZdyQDgDLcPNzuw0E=</X509Certificate>
2005/05/identity/claims/emailaddress" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="E-Mail Address"/>
<Attribute </X509Data>
</KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="signing"xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Given Name"/>
<Attribute <KeyInfo xmlnsxmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://wwwschemas.w3xmlsoap.org/2000ws/09/xmldsig#">
<X509Data>
<X509Certificate>EBAQUAA4IBDwAwggEKAoIBAQCvWpfMCOsjYgkuOwOzCGLjH9bbECRZ6U1uSrtr/xxi54vLaIVhKotqKUN2nKEem8LDMIgi4zlSsqoNgaoKyn7+o99wN+9bD4jd9KZsqSfY4u7DF49MNZ5lydj/yx8jpuXBcvMHstoPQWFRw6HWgm5/vQlmoZrbBjahfPvCajxxJWjYZvjdhEDBaPZcpTeSPsMME8fdEgG07NaUW0EjkI4on9CsNv1RfQkplpDnePa5Swfjv1V5BIOtBZWuCCDIANv+CkRHcpZBvmYVzG/SNOnLMRBp6Skz37+JqlYdzQ0W5NyFoYzzKOqhDndEGxHRUWbujknHqIaD9CkCg2jT16q9AgMBAAEwDQYJKoZIhvcNAQELBQADggEBAIt1d96VNKbxNwjoxjQ678aamseXPoJsusSJpyiwXiVX7OFiESNQrdQ77Xe8wMccKYMZvb7ESUKhOfRBx9sS/nb6WpujCTfeiP+DR9n3QGTDrsPM6+gOK45svKus8zhVb+Ml+I6WC7iGA9WlJj2LMRR989AlcABFv10Bssqan835EU43lQrSnoS9GJTByykO7JuSjNXvgupcREE9BWgJRSfQ9U9P/r9hBVwjWT4K6gtx4Vws48vfEpY19owx09WJFaJIi4SbcTX/Mi1lyk5wmUfR6t+KHj8eoKvoyuqb/eAPjvVlr7Ktw0xOuWxt7IptGwHVV13x8arNkHb/qMrXtb0=</X509Certificate>
</X509Data>
</KeyInfo>
</KeyDescriptor>2005/05/identity/claims/name" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Name"/>
<SingleLogoutService<Attribute Bindingxmlns="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirectassertion" LocationName="httpshttp://YourAdfsServerschemas.test.edu/adfs/ls/"/>
<SingleLogoutService Bindingxmlsoap.org/ws/2005/05/identity/claims/upn" NameFormat="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://YourAdfsServer.test.edu/adfs/ls/attrname-format:uri" FriendlyName="UPN"/>
<NameIDFormat>urn<Attribute xmlns="urn:oasis:names:tc:SAML:12.1:nameid-format:emailAddress</NameIDFormat>
<NameIDFormat>urn0:assertion" Name="http://schemas.xmlsoap.org/claims/CommonName" NameFormat="urn:oasis:names:tc:SAML:2.0:nameidattrname-format:persistent</NameIDFormat>uri" FriendlyName="Common Name"/>
<Attribute <NameIDFormat>urnxmlns="urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<SingleSignOnService Bindingassertion" Name="http://schemas.xmlsoap.org/claims/EmailAddress" NameFormat="urn:oasis:names:tc:SAML:2.0:bindings:HTTPattrname-Redirectformat:uri" LocationFriendlyName="https://YourAdfsServer.test.edu/adfs/ls/AD FS 1.x E-Mail Address"/>
<SingleSignOnService<Attribute Bindingxmlns="urn:oasis:macenames:tc:shibbolethSAML:12.0:profiles:AuthnRequestassertion" LocationName="httpshttp://YourAdfsServerschemas.testxmlsoap.eduorg/adfsclaims/ls/Group"/>
<SingleSignOnService Binding NameFormat="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POSTattrname-format:uri" LocationFriendlyName="https://YourAdfsServer.test.edu/adfs/ls/Group"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddressUPN" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="E-Mail AddressAD FS 1.x UPN"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws/20052008/0506/identity/claims/givennamerole" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Given NameRole"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/namesurname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="NameSurname"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upnprivatepersonalidentifier" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="UPNPPID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/CommonNamenameidentifier" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="CommonName NameID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.orgmicrosoft.com/ws/2008/06/identity/claims/EmailAddressauthenticationinstant" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ADAuthentication FS 1.x E-Mail Addresstime stamp"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.orgmicrosoft.com/ws/2008/06/identity/claims/Groupauthenticationmethod" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="GroupAuthentication method"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/UPNdenyonlysid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ADDeny FSonly 1.xgroup UPNSID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/roledenyonlyprimarysid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="RoleDeny only primary SID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws/20052008/0506/identity/claims/surnamedenyonlyprimarygroupsid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SurnameDeny only primary group SID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws/20052008/0506/identity/claims/privatepersonalidentifiergroupsid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="PPIDGroup SID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws/20052008/0506/identity/claims/nameidentifierprimarygroupsid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="NamePrimary group IDSID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationinstantprimarysid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="AuthenticationPrimary time stampSID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethodwindowsaccountname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="AuthenticationWindows account methodname"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws2012/200501/05devicecontext/identity/claims/denyonlysidisregistereduser" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DenyIs onlyRegistered group SIDUser"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/20082012/0601/identitydevicecontext/claims/denyonlyprimarysididentifier" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Deny only primary SIDDevice Identifier"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws2012/200801/06/identitydevicecontext/claims/denyonlyprimarygroupsidregistrationid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DenyDevice only primary group SIDRegistration Identifier"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws2012/200801/06devicecontext/identity/claims/groupsiddisplayname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="GroupDevice Registration SIDDisplayName"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws2012/200801/06/identitydevicecontext/claims/primarygroupsidostype" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="PrimaryDevice groupOS SIDtype"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws2012/200801/06devicecontext/identity/claims/primarysidosversion" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="PrimaryDevice OS SIDVersion"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws2012/200801/06/identitydevicecontext/claims/windowsaccountnameismanaged" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="WindowsIs accountManaged nameDevice"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser/requestcontext/claims/x-ms-forwarded-client-ip" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="IsForwarded RegisteredClient UserIP"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/identifierx-ms-client-application" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DeviceClient IdentifierApplication"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/registrationidx-ms-client-user-agent" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DeviceClient RegistrationUser IdentifierAgent"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/displaynamex-ms-client-ip" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DeviceClient Registration DisplayNameIP"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/ostypex-ms-endpoint-absolute-path" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="DeviceEndpoint OS typePath"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/osversionx-ms-proxy" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Device OS VersionProxy"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/01/devicecontextrequestcontext/claims/ismanagedrelyingpartytrustid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="IsApplication Managed DeviceIdentifier"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-forwarded-client-ipextension/applicationpolicy" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ForwardedApplication Client IPpolicies"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-client-applicationextension/authoritykeyidentifier" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ClientAuthority Key ApplicationIdentifier"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-client-user-agentextension/basicconstraints" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ClientBasic User AgentConstraint"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-client-ipextension/eku" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ClientEnhanced Key IPUsage"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-endpoint-absolute-pathfield/issuer" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Endpoint PathIssuer"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claims/x-ms-proxyfield/issuername" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ProxyIssuer Name"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/0112/requestcontextcertificatecontext/claimsextension/relyingpartytrustidkeyusage" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ApplicationKey IdentifierUsage"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extensionfield/applicationpolicynotafter" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ApplicationNot policiesAfter"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extensionfield/authoritykeyidentifiernotbefore" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="AuthorityNot Key IdentifierBefore"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extension/basicconstraintscertificatepolicy" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="BasicCertificate ConstraintPolicies"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoftxmlsoap.comorg/ws/20122005/1205/certificatecontextidentity/extensionclaims/ekursa" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="EnhancedPublic Key Usage"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/field/issuerrawdata" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="IssuerCertificate Raw Data"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/fieldextension/issuernamesan" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="IssuerSubject Alternative Name"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/20122008/1206/certificatecontextidentity/extensionclaims/keyusageserialnumber" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="KeySerial UsageNumber"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/field/notaftersignaturealgorithm" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="NotSignature AfterAlgorithm"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/field/notbeforesubject" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Not BeforeSubject"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extension/certificatepolicysubjectkeyidentifier" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="CertificateSubject Key PoliciesIdentifier"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws2012/200512/05certificatecontext/identityfield/claims/rsasubjectname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="PublicSubject KeyName"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/fieldextension/rawdatacertificatetemplateinformation" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="CertificateV2 RawTemplate DataName"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extension/sancertificatetemplatename" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SubjectV1 AlternativeTemplate Name"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoftxmlsoap.comorg/ws/20082005/0605/identity/claims/serialnumberthumbprint" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Serial NumberThumbprint"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/field/signaturealgorithmx509version" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SignatureX.509 AlgorithmVersion"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2012/12/certificatecontext/field/subject01/insidecorporatenetwork" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SubjectInside Corporate Network"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2012/12/certificatecontext/extension/subjectkeyidentifier01/passwordexpirationtime" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SubjectPassword KeyExpiration IdentifierTime"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2012/12/certificatecontext/field/subjectname01/passwordexpirationdays" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="SubjectPassword Expiration NameDays"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/ws/2012/12/certificatecontext/extension/certificatetemplateinformation01/passwordchangeurl" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="V2Update TemplatePassword NameURL"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.microsoft.com/2012/12/certificatecontext/extension/certificatetemplatenameclaims/authnmethodsreferences" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="V1Authentication TemplateMethods NameReferences"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas.xmlsoapmicrosoft.orgcom/ws2012/200501/05/identityrequestcontext/claims/thumbprintclient-request-id" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="ThumbprintClient Request ID"/>
<Attribute xmlns="urn:oasis:names:tc:SAML:2.0:assertion" Name="http://schemas</IDPSSODescriptor>
</EntityDescriptor> |
|---|
|
AD FS Claim Creation
AD FS installation and configuration isn't covered in this guide. If you need help please see here: https://technet.microsoft.com/
...
en-us/
...
library/dn486820(v=ws.11).aspx Once AD FS is installed the below Powershell script will create a "Relaying Party Trust" with the name CCCPilot.
(You will need your MISnnn code first discussed here: https://cccnext.jira.com/wiki/display/CSF/Steps+to+Integrate+with+the+CCC+SSO+Proxy follow the step to get the MISnnn code.):
(AD FS PowerShell tools must be active run "Add-PSSnapin Microsoft.Adfs.PowerShell" if needed. Add your MIS number in place of MISnnn)
Add-AdfsRelyingPartyTrust -Name "CCCPilot" -MetadataUrl https://sso.pilot.cccmypath.org/simplesaml/module.php/saml/sp/metadata.php/MISnnn |
|---|
You should see the Relaying Party Trust listed:
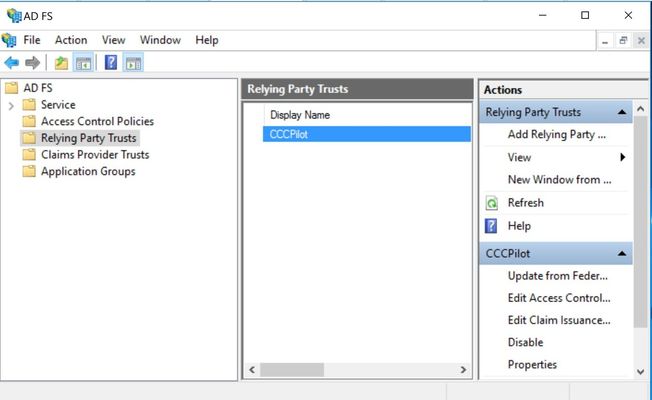 Image Added
Image Added
You can edit the Claim Issuance Policy manually from this page, but it's a very time consuming task. Below is a PowerShell script that can add the policies for you.
First, create a powershell script in a directory named ClaimPolicy.ps1 and copy the below. Edit the "Target Identifier" to match what is listed in AD FS.
Set-AdfsRelyingPartyTrust -TargetIdentifier https://YourTargetIdentifier -IssuanceTransformRulesFile rules.inc -SignatureAlgorithm http://www.w3.org/2000/09/xmldsig#rsa-sha1 -IssuanceAuthorizationRules '=> issue(Type = "http://schemas.microsoft.com/ |
|---|
...
...
AD FS Claim Creation
AD FS installation and configuration isn't covered in this guide. If you need help please see here: https://technet.microsoft.com/en-us/library/dn486820(v=ws.11).aspx Once AD FS is installed the below Powershell script will create a "Relaying Party Trust" with the name CCCPilot.
(You will need your MISnnn code first discussed here: https://cccnext.jira.com/wiki/display/CSF/Steps+to+Integrate+with+the+CCC+SSO+Proxy follow the step to get the MISnnn code.):
(AD FS PowerShell tools must be active run "Add-PSSnapin Microsoft.Adfs.PowerShell" if needed. Add your MIS number in place of MISnnn)
...
Add-AdfsRelyingPartyTrust -Name "CCCPilot" -MetadataUrl https://sso.pilot.cccmypath.org/simplesaml/module.php/saml/sp/metadata.php/MISnnn
You should see the Relaying Party Trust listed:
 Image Removed
Image Removed
You can edit the Claim Issuance Policy manually from this page, but it's a very time consuming task. Below is a PowerShell script that can add the policies for you.
First, create a powershell script in a directory named ClaimPolicy.ps1 and copy the below. Edit the "Target Identifier" to match what is listed in AD FS.
Set-AdfsRelyingPartyTrust -TargetIdentifier https://YourTargetIdentifier -IssuanceTransformRulesFile rules.inc -SignatureAlgorithm http://www.w3.org/2000/09/xmldsig#rsa-sha1 -IssuanceAuthorizationRules 'permit", Value = "true");'
|
|---|
In the same directory where ClaimPolicy.ps1 is stored create a file named rules.inc and copy the below policies as needed. The below are samples of claim transformations described in the Microsoft article. Not all of the examples will match your environment but you can modify the below to fit your needs. Refer to https://msdn.microsoft.com/en-us/library/ms675090(v=vs.85).aspx for a list of all Active Directory attributes. A list of attributes we require can be found here: Attributes for CCC SSO Federated Access For the most part, these attributes should match your environment. The next section below will have examples of the "edu" specific attributes and those will need to match what you have stored in your AD. Consider what is listed as a placeholder.
The first rule requests the attribute from AD and the second rule converts the attribute to the format expected by SimpleSAMLphp & Shibboleth.
@Rulename="Get Email"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:0.9.2342.19200300.100.1.3"), query = ";mail;{0}", param = c.Value);
@Rulename="Convert Email xml"
c:[Type == "urn:oid:0.9.2342.19200300.100.1.3"]
=> issue(Type = "http://schemas.microsoft.com/authorization/claims/permit"c.Type, Value = "true");'
|
|---|
In the same directory where ClaimPolicy.ps1 is stored create a file named rule.inc and copy the below policies as needed. The below are samples of claim transformations described in the Microsoft article. Not all of the examples will match your environment but you can modify the below to fit your needs. Refer to https://msdn.microsoft.com/en-us/library/ms675090(v=vs.85).aspx for a list of all Active Directory attributes. A list of attributes we require can be found here: Attributes for CCC SSO Federated Access For the most part, these attributes should match your environment. The next section below will have examples of the "edu" specific attributes and those will need to match what you have stored in your AD. Consider what is listed as a placeholder.
The first rule requests the attribute from AD and the second rule converts the attribute to the format expected by SimpleSAMLphp & Shibboleth.
@Rulename="Get Emailc.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName="Get FirstName"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:02.95.2342.19200300.100.1.34.42"), query = ";mailgivenName;{0}", param = c.Value);
@Rulename@RuleName="Convert EmailFirstName xml"
c:[Type == "urn:oid:02.95.2342.19200300.100.1.34.42"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName="Get FirstNameLastName"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.424"), query = ";givenNamesn;{0}", param = c.Value);
@RuleName="Convert FirstNameLastName xml"
c:[Type == "urn:oid:2.5.4.424"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName@Rulename="Get LastNamesAMAaccountName"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:1.2.840.5113556.1.4.4221"), query = ";snsAMAccountName;{0}", param = c.Value);
@RuleName@Rulename="Convert sAMAccountName / LastNameuid xml"
c:[Type == "urn:oid:1.2.840.113556.51.4.4221"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["urn:oid:0.9.2342.19200300.100.1.1", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri"); @Rulename="Get displayName" c:[Type == "http://schemas.xmlsoapmicrosoft.orgcom/ws/20052008/0506/identity/claimproperties/attributenameclaims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oasis:names:tc:SAML:2.0:attrname-format:uri"); oid:1.2.840.113556.1.2.13"), query = ";displayName;{0}", param = c.Value);
@Rulename="GetConvert displayName sAMAaccountNamexml"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:1.2.840.113556.1.4.221"), query = ";uid;{0}", param = c.Value);
@Rulename="Convert sAMAccountName / uid xml"
urn:oid:1.2.840.113556.1.2.13"]
=> issue(Type = "urn:oid:2.16.840.1.113730.3.1.241", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Name Identifier"c:[Type == "urn:oid:1.2.840.113556.1.4.221"]
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"] => issue(Type = "urn:oid:1.3.6.1.4.1.5923.1.1.1.5", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimpropertiesclaims/attributenamenameidentifier"], Issuer = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Get displayName"
c:[Type == c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.microsoftxmlsoap.comorg/ws/20082005/0605/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:1.2.840.113556.1.2.13"), query = ";displayName;{0}", param = c.Value);
@Rulename="Convert displayName xml"
claimproperties/format"] = "urn:oasis:names:tc:SAML:2.0:nameid-format:transient"); |
|---|
Example of eduPersonPrinipalName(EPPN) mapped to upn. Any value you use should be a unique value that won't change. You need to modify the member@yourdomain.edu in the Value property to match your domain. This is a scoped attribute.
@Rulename="Transform sAMAccountName to EPPN" c:[Type == "urn:oid:1.2.840.113556.1.2.13"]
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"] => issue(Type = "urn:oid:2.16.8401.3.6.1.4.1.5923.113731.31.1.2416", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
|
|---|
Example of
...
eduPersonPrincipalName(EPPN) mapped to sAMAccountName. Like the above example, the EPPN needs to be unique not only to your organization but to others as well. The sAMAccountName doesn't have the domain value added, the below example you create three custom rules. The first queries AD for sAMAccountName & upn, the second pulls the domain value from the upn, the third adds the domain value to the sAMAccountName and gives it the EPPN value.
@Rulename="Query AD for upn and sAMAccountName" c:[Type == "http://schemas. |
|---|
xmlsoaporg200505upnwindowsaccountname", Issuer == "AD AUTHORITY"]
|
|---|
issueTypeurn:oid:1.3.6.1.4.1.5923.1.1.1.6Valuec.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Transform EPPN & add scope"
("ssupn", "sswindowsaccountname"), query = ";userPrincipalName,sAMAccountName;{0}", param = c.Value);
@Rulename="Obtain the domain from the upn"
c:[Type == |
|---|
"http://schemas.xmlsoap.org/claims/Group", Value"ssupn"]
=> add(Type = "ssnewupn", Value = RegExReplace(c.Value, "^(.*?)@", ""));
@Rulename="Combine sAMAccountName with domain"
c1:[Type == " |
|---|
Domain Usersssnewupn"]
&& c2:[Type == "sswindowsaccountname"]
=> issue(Type = "urn:oid:1.3.6.1.4.1.5923.1.1.1.6", Value = |
|---|
"member@yourdomain.edu"c2.Value + "@" + c1.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri"); |
|---|
Example of eduPersonAffiliation stored in title:
...
@RuleName="Query group membership for student"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "S-1-5-21-378740516-3305441437-1085053907-1122", Issuer == "AD AUTHORITY"]
=> issue(Type = "http://schemas.xmlsoap.org/claims/Group", Value = "student", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName="Return value of group membership and send eduPersonPrimaryAffilationeduPersonAffilation if student"
c:[Type == "http://schemas.xmlsoap.org/claims/Group", Value == "student"]
=> issue(Type = "urn:oid:1.3.6.1.4.1.5923.1.1.1.51", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName="Query group membership for staff"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "S-1-5-21-378740516-3305441437-1085053907-1123", Issuer == "AD AUTHORITY"]
=> issue(Type = "http://schemas.xmlsoap.org/claims/Group", Value = "studentstaff", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@RuleName="Return value of group membership and send eduPersonPrimaryAffilationeduPersonAffilation if staff"
c:[Type == "http://schemas.xmlsoap.org/claims/Group", Value == "staff"]
=> issue(Type = "urn:oid:1.3.6.1.4.1.5923.1.1.1.51", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
|
|---|
...
@Rulename="Get cccId stored in description field"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.13"), query = ";description;{0}", param = c.Value);
@Rulename="Convert cccId / description xml"
c:[Type == "urn:oid:2.5.4.13"]
=> issue(Type = "https://www.openccc.net/saml/attributes/cccId", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri"); |
|---|
...
@Rulename="Get Street"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.9"), query = ";street;{0}", param = c.Value);
@Rulename="Convert Street xml"
c:[Type == "urn:oid:2.5.4.9"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Get Locality"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.7"), query = ";l;{0}", param = c.Value);
@Rulename="Convert Locality xml"
c:[Type == "urn:oid:2.5.4.7"]
=> issue(Type = "urn:oid:2.5.4.7", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Get State"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.8"), query = ";st;{0}", param = c.Value);
@Rulename="Convert State xml"
c:[Type == "urn:oid:2.5.4.8"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Get PostalCode"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.17"), query = ";postalCode;{0}", param = c.Value);
@Rulename="Convert PostalCode xml"
c:[Type == "urn:oid:2.5.4.17"]
=> issue(Type = c.Type, Value = c.Value, Issuer = c.Issuer, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Get telephoneNumber / homePhone"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:2.5.4.20"), query = ";telephoneNumber;{0}", param = c.Value);
@Rulename="Convert telephoneNumber xml"
c:[Type == "urn:oid:2.5.4.20"]
=> issue(Type = "urn:oid:0.9.2342.19200300.100.1.20", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
@Rulename="Example Get Manager add domain"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("urn:oid:0.9.2342.19200300.100.1.10"), query = ";manager;{0}", param = c.Value); |
|---|
Note for CCC Tech Center implementations: AD FS metadata isn't compatible with the proxy. Use the attached template and modify with the data supplied in the college's metadata.| View file |
|---|
| name | ADFS_Metadata_template.zip |
|---|
| height | 250 |
|---|
|
...